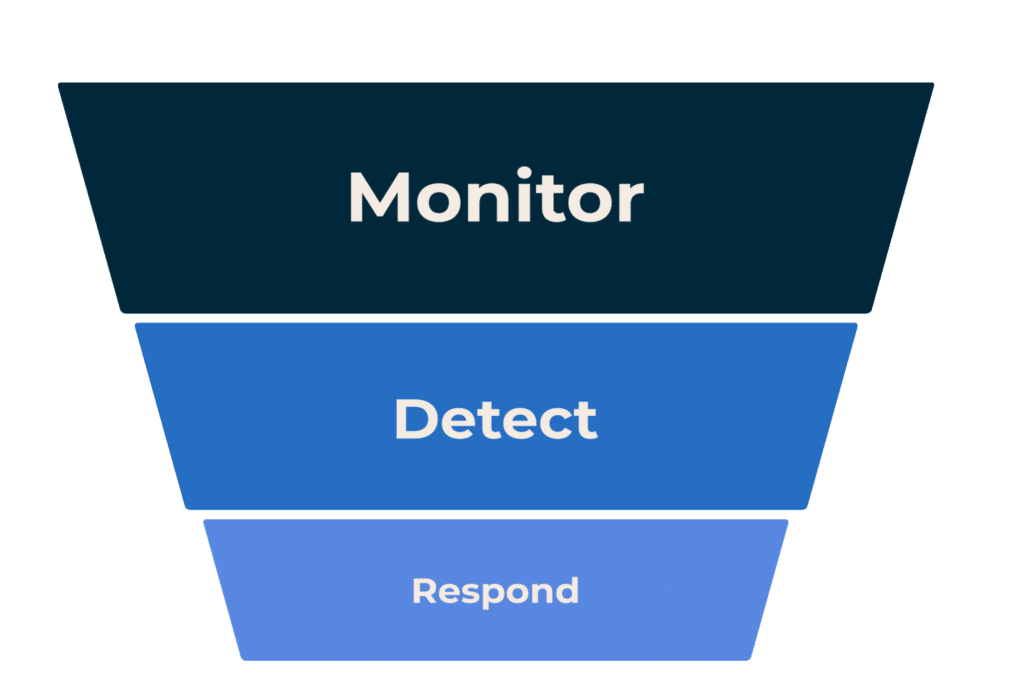
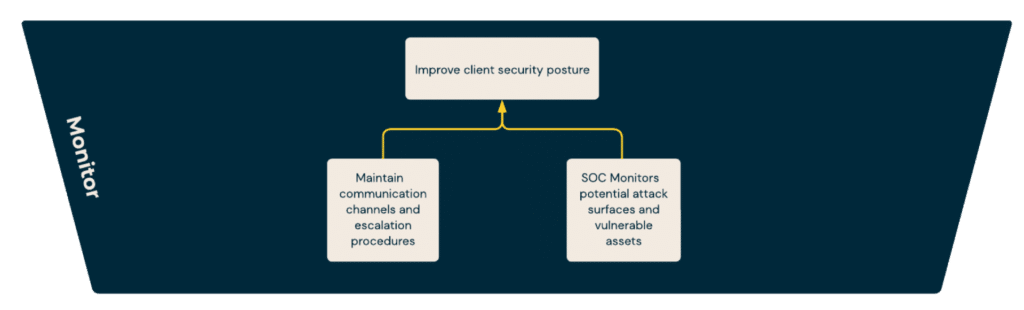
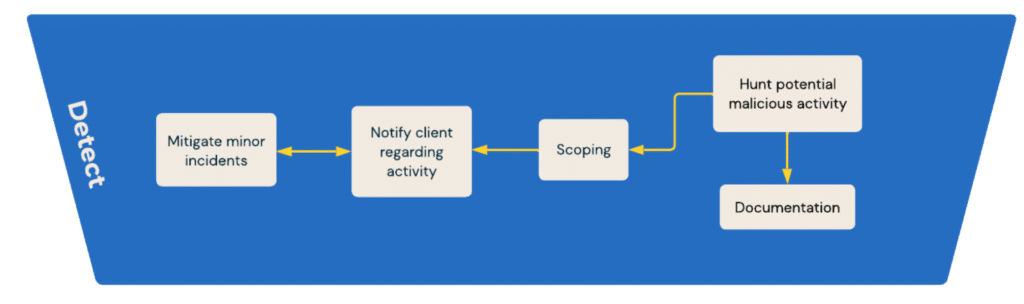
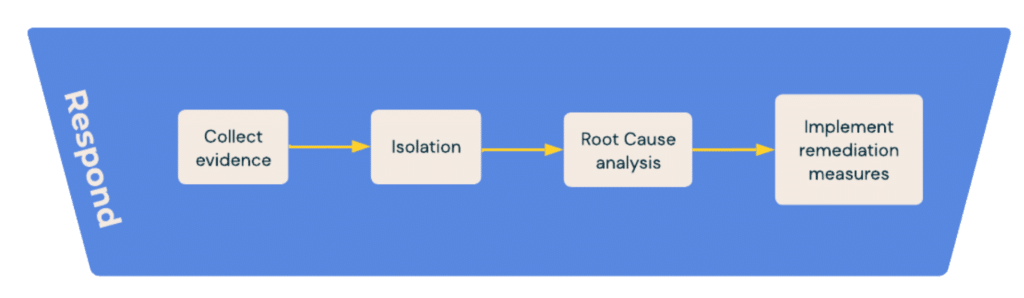
In today’s fast-paced digital realm, environments are increasingly characterized by volatility, uncertainty, complexity, and ambiguity (VUCA). Effective cybersecurity in such a landscape demands not just agility but also precise decision-making – a balance that many fail to strike. At Blueshift Cybersecurity, we provide a new approach to incident response.