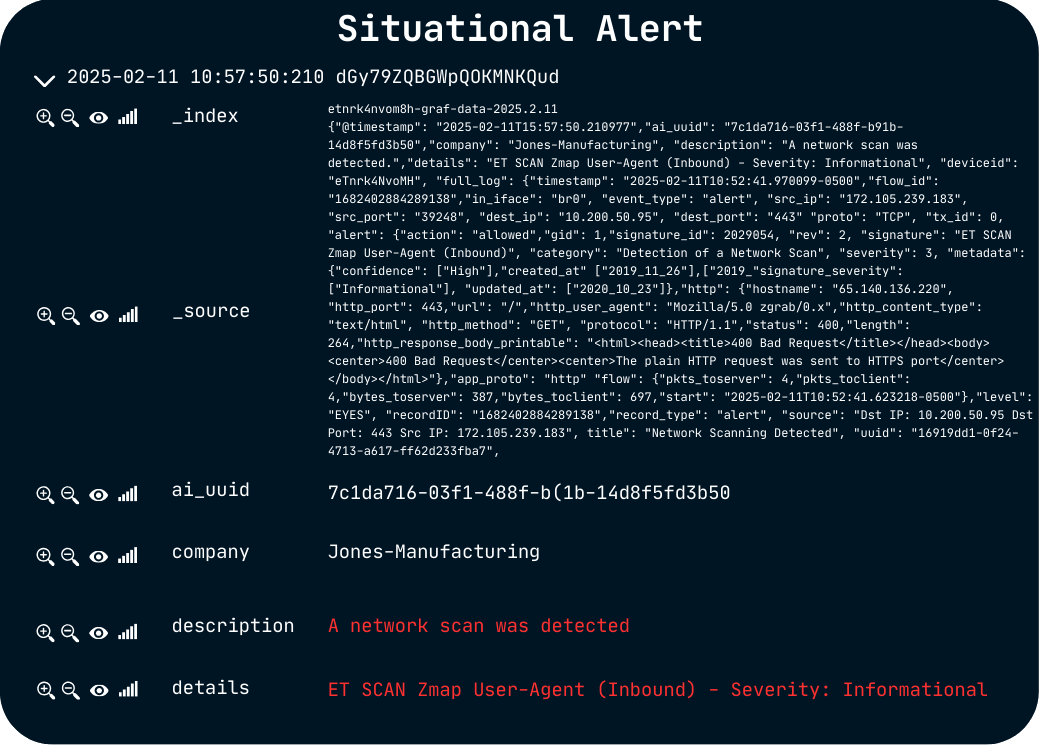
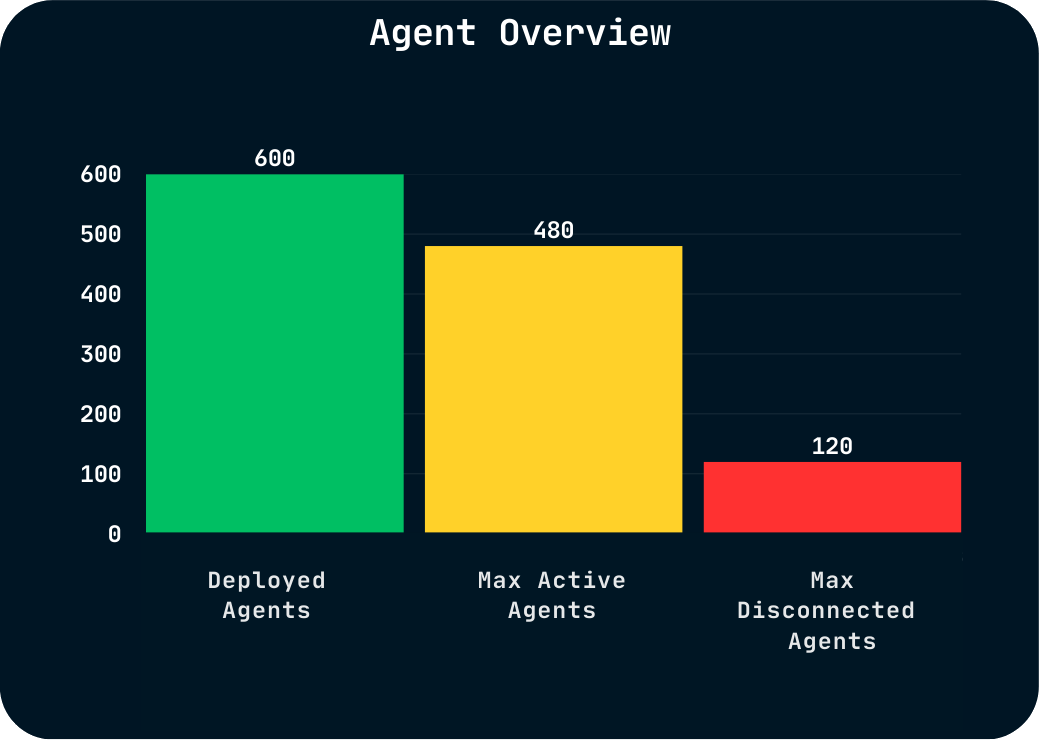
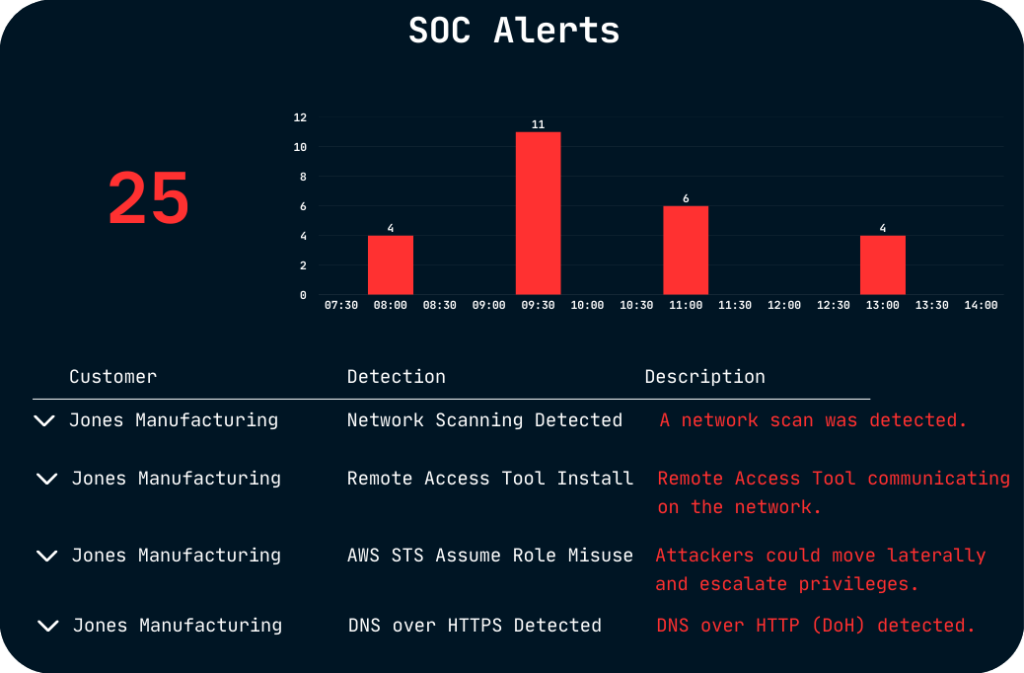
“After reviewing several SOC-as-a-Service providers, we found Blueshift’s technology, ease of deployment, customizability and ability to monitor all devices connected to the network to be far ahead of the competition.
Blueshift’s unique combination of technology and world-class cybersecurity operations truly provides protection against attacks other solutions miss.”